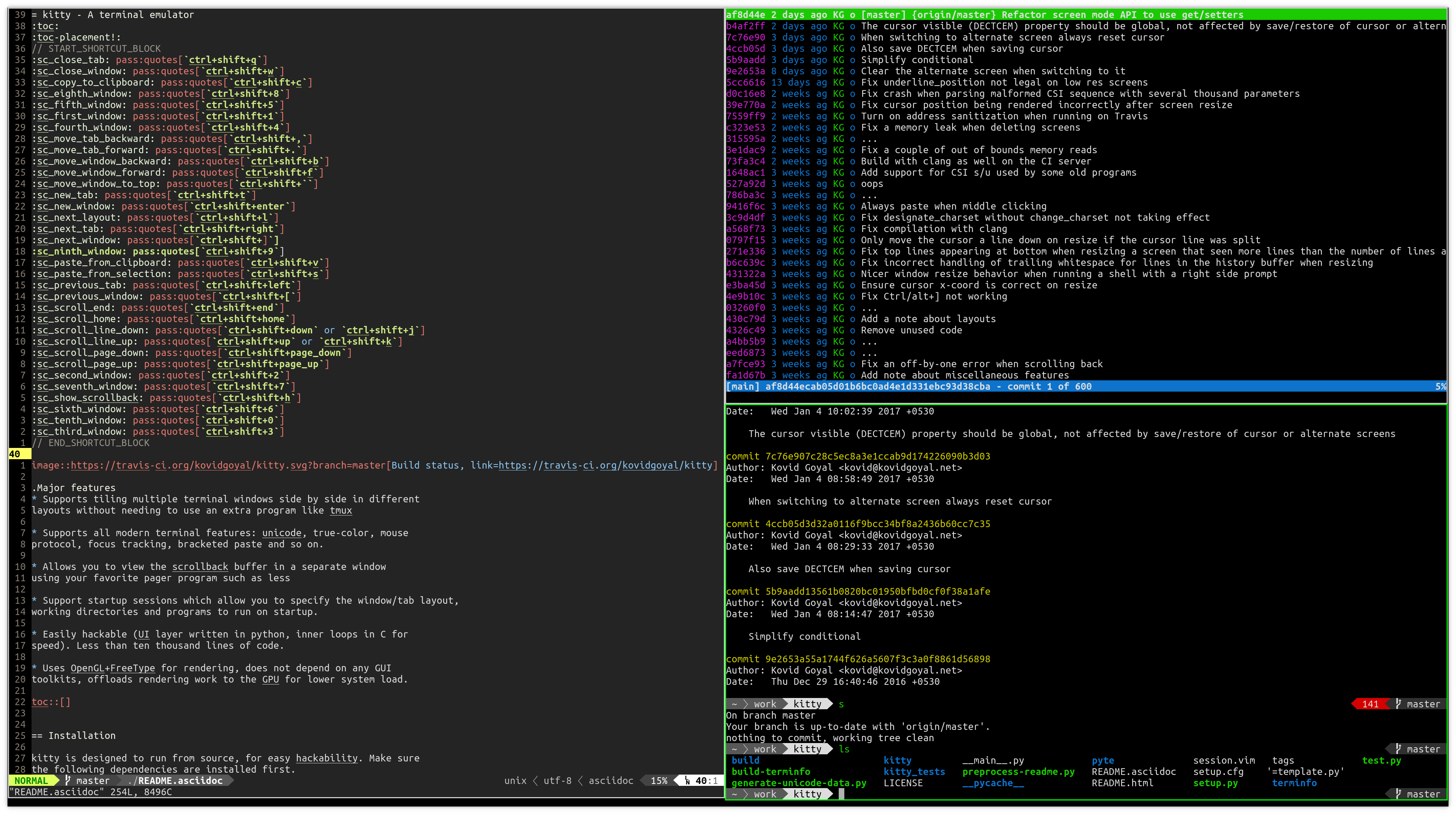
For the past year, we have been collecting feedback on how we can make Tor Browser work better for you.
Tor Browser 8.0, our first stable release based on Firefox 60 ESR, is now available from the Tor Browser Project page and also from our distribution directory. This release is all about users first.
Tor Browser 8.0 comes with a series of user experience improvements that address a set of long-term Tor Browser issues you’ve told us about. To meet our users' needs, Tor Browser has a new user onboarding experience; an updated landing page that follows our styleguide; additional language support; and new behaviors for bridge fetching, displaying a circuit, and visiting .onion sites.
New User Onboarding
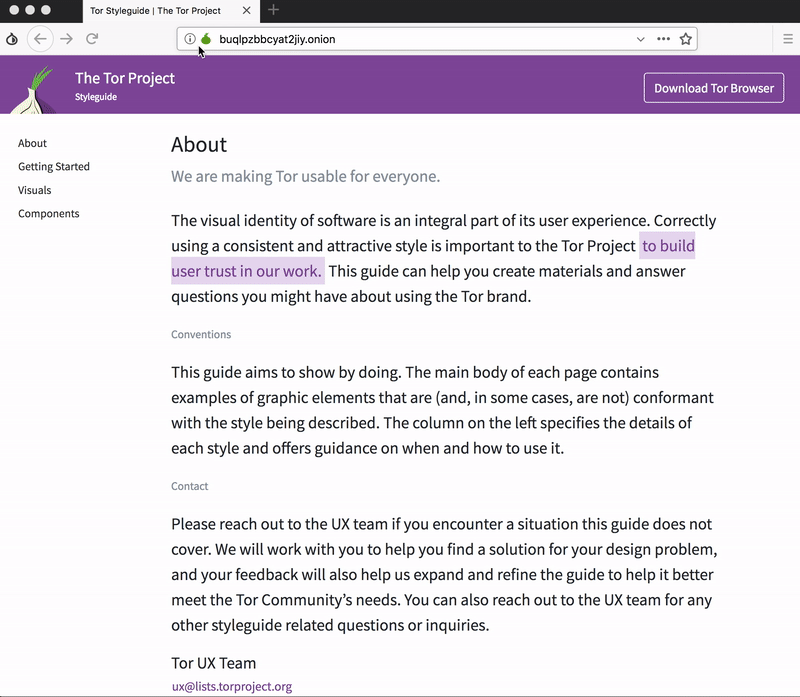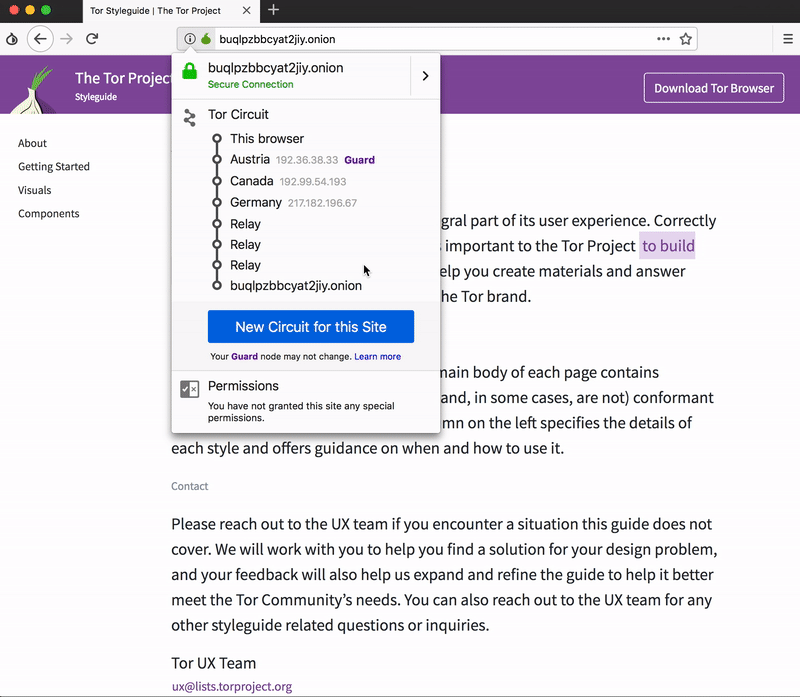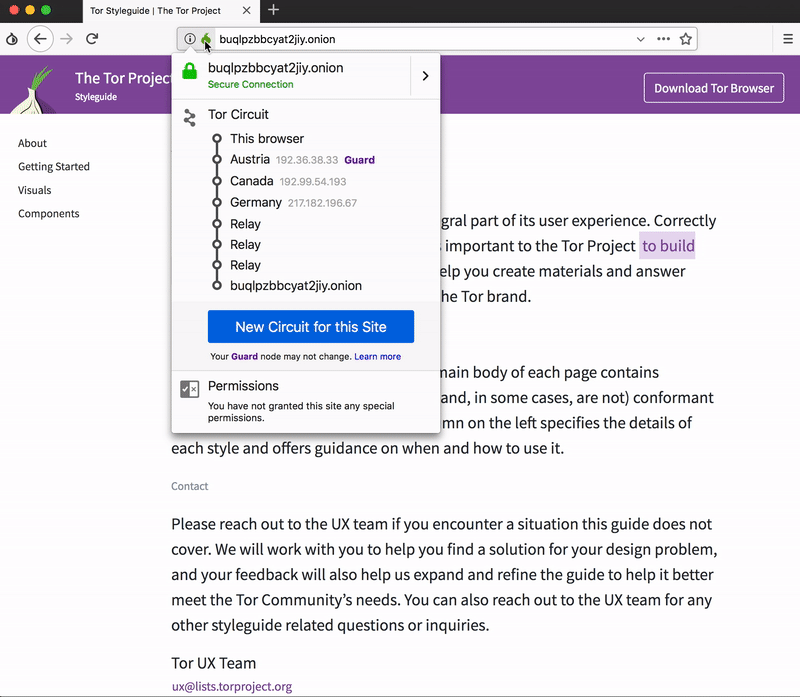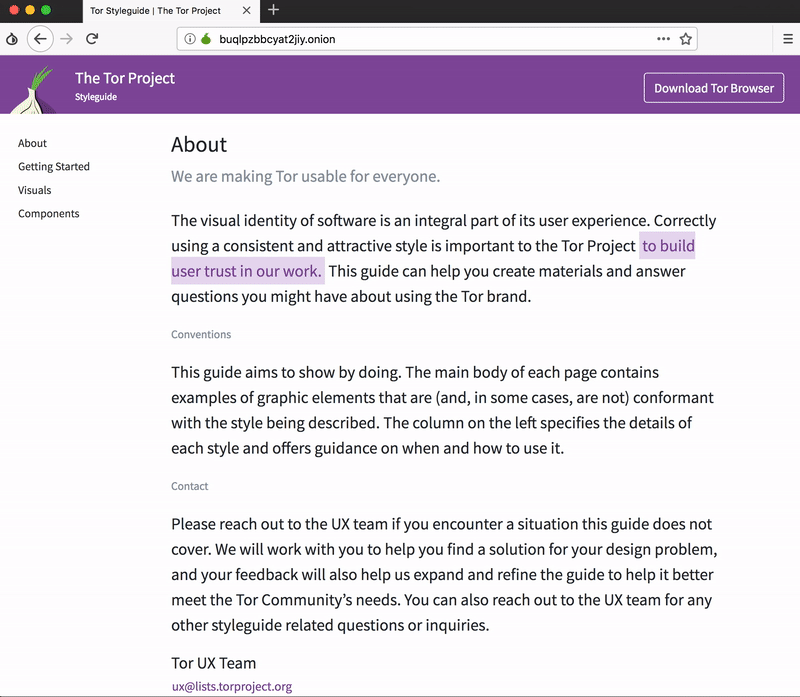
For the most part, using Tor is like using any other browser (and it is based on Firefox), but there are some usage differences and cool things happening behind the scenes that users should be aware of. Our new onboarding experience aims to better let you know about unique aspects of Tor Browser and how to maximize those for your best browsing experience.
Improved Bridge Fetching
For users where Tor is blocked, we have previously offered a handful of bridges in the browser to bypass censorship. But to receive additional bridges, you had to send an email or visit a website, which posed a set of problems. To simplify how you request bridges, we now have a new bridge configuration flow when you when you launch Tor. Now all you have to do is solve a captcha in Tor Launcher, and you’ll get a bridge IP. We hope this simplification will allow more people to bypass censorship and browse the internet freely and privately.
Better Language Support
Millions of people around the world use Tor, but not everyone has been able to use Tor in their language. In Tor Browser 8, we’ve added resources and support for nine previously unsupported languages: Catalan, Irish, Indonesian, Icelandic, Norwegian, Danish, Hebrew, Swedish, and Traditional Chinese.
Apart from those highlights, a number of other component and toolchains got an update for this major release. In particular, we now ship Tor 0.3.3.9 with OpenSSL 1.0.2p and Libevent 2.1.8. Moreover, we switched to the pure WebExtension version of NoScript (version 10.1.9.1) which we still need to provide the security slider functionality. Additionally, we start shipping 64bit builds for Windows users which should enhance Tor Browser stability compared to the 32bit bundles.
Providing this many improvements for our users could only be possible with collaboration between the Tor Browser team and Tor's UX team, Community team, Services Admin team, and our volunteers. We would like to thank everyone for working hard over the past year to bring all these new features to our users.
Known Issues
We already collected a number of unresolved bugs since Tor Browser 7.5.6 and tagged them with our ff60-esr keyword to keep them on our radar. The most important ones are listed below:
- WebGL is broken right now.
- We disable Stylo on macOS due to reproducibility issues we need to investigate and fix. This will likely not get fixed for Tor Browser 8, as we need some baking time on our nightly/alpha channel before we are sure there are no reproducibility/stability regressions. The tentative plan is to get it ready for Tor Browser 8.5.
Note: This release is signed with a new GPG subkey as the old one expired a couple of days ago. You might need to refresh your copy of the public part of the Tor Browser signing key before doing the verification. The fingerprint of the new subkey is 1107 75B5 D101 FB36 BC6C 911B EB77 4491 D9FF 06E2.
Give Feedback
This is only the beginning of our efforts to put users first. If you find a bug or have a suggestion for how we could improve this release, please let us know.
Changelog
The full changelog since Tor Browser 7.5.6 is:
- All platforms
- Update Firefox to 60.2.0esr
- Update Tor to 0.3.3.9
- Update OpenSSL to 1.0.2p
- Update Libevent to 2.1.8
- Update Torbutton to 2.0.6
- Bug 26960: Implement new about:tor start page
- Bug 26961: Implement new user onboarding
- Bug 26962: Circuit display onboarding
- Bug 27301: Improve about:tor behavior and appearance
- Bug 27214: Improve the onboarding text
- Bug 26321: Move 'New Identity', 'New Circuit' to File, hamburger menus
- Bug 26100: Adapt Torbutton to Firefox 60 ESR
- Bug 26520: Fix sec slider/NoScript for TOR_SKIP_LAUNCH=1
- Bug 27401: Start listening for NoScript before it loads
- Bug 26430: New Torbutton icon
- Bug 24309: Move circuit display to the identity popup
- Bug 26884: Use Torbutton to provide security slider on mobile
- Bug 26128: Adapt security slider to the WebExtensions version of NoScript
- Bug 27276: Adapt to new NoScript messaging protocol
- Bug 23247: Show security state of .onions
- Bug 26129: Show our about:tor page on startup
- Bug 26235: Hide new unusable items from help menu
- Bug 26058: Remove workaround for hiding 'sign in to sync' button
- Bug 26590: Use new svg.disabled pref in security slider
- Bug 26655: Adjust color and size of onion button
- Bug 26500: Reposition circuit display relay icon for RTL locales
- Bug 26409: Remove spoofed locale implementation
- Bug 26189: Remove content-policy.js
- Bug 26490: Remove the security slider notification
- Bug 25126: Make about:tor layout responsive
- Bug 27097: Add text for Tor News signup widget
- Bug 21245: Add da translation to Torbutton and keep track of it
- Bug 27129+20628: Add locales ca, ga, id, is, nb, da, he, sv, and zh-TW
- Translations update
- Update Tor Launcher to 0.2.16.3
- Bug 23136: Moat integration (fetch bridges for the user)
- Bug 25750: Update Tor Launcher to make it compatible with Firefox 60 ESR
- Bug 26985: Help button icons missing
- Bug 25509: Improve the proxy help text
- Bug 26466: Remove sv-SE from tracking for releases
- Bug 27129+20628: Add locales ca, ga, id, is, nb, da, he, sv, and zh-TW
- Translations update
- Update HTTPS Everywhere to 2018.8.22
- Update NoScript to 10.1.9.1
- Update meek to 0.31
- Bug 26477: Make meek extension compatible with ESR 60
- Update obfs4proxy to v0.0.7 (bug 25356)
- Bug 27082: Enable a limited UITour for user onboarding
- Bug 26961: New user onboarding
- Bug 26962: New feature onboarding
- Bug 27403: The onboarding bubble is not always displayed
- Bug 27283: Fix first-party isolation for UI tour
- Bug 27213: Update about:tbupdate to new (about:tor) layout
- Bug 14952+24553: Enable HTTP2 and AltSvc
- Bug 25735: Tor Browser stalls while loading Facebook login page
- Bug 17252: Enable TLS session identifiers with first-party isolation
- Bug 26353: Prevent speculative connects that violate first-party isolation
- Bug 26670: Make canvas permission prompt respect first-party isolation
- Bug 24056: Use en-US strings in HTML forms if locale is spoofed to english
- Bug 26456: HTTP .onion sites inherit previous page's certificate information
- Bug 26561: .onion images are not displayed
- Bug 26321: Move 'New Identity', 'New Circuit' to File, hamburger menus
- Bug 26833: Backport Mozilla's bug 1473247
- Bug 26628: Backport Mozilla's bug 1470156
- Bug 26237: Clean up toolbar for ESR60-based Tor Browser
- Bug 26519: Avoid Firefox icons in ESR60
- Bug 26039: Load our preferences that modify extensions (fixup)
- Bug 26515: Update Tor Browser blog post URLs
- Bug 26216: Fix broken MAR file generation
- Bug 26409: Remove spoofed locale implementation
- Bug 25543: Rebase Tor Browser patches for ESR60
- Bug 23247: Show security state of .onions
- Bug 26039: Load our preferences that modify extensions
- Bug 17965: Isolate HPKP and HSTS to URL bar domain
- Bug 21787: Spoof en-US for date picker
- Bug 21607: Disable WebVR for now until it is properly audited
- Bug 21549: Disable wasm for now until it is properly audited
- Bug 26614: Disable Web Authentication API until it is properly audited
- Bug 27281: Enable Reader View mode again
- Bug 26114: Don't expose navigator.mozAddonManager to websites
- Bug 21850: Update about:tbupdate handling for e10s
- Bug 26048: Fix potentially confusing "restart to update" message
- Bug 27221: Purge startup cache if Tor Browser version changed
- Bug 26049: Reduce delay for showing update prompt to 1 hour
- Bug 26365: Add potential AltSvc support
- Bug 9145: Fix broken hardware acceleration on Windows and enable it
- Bug 26045: Add new MAR signing keys
- Bug 25215: Revert bug 18619 (we are not disabling IndexedDB any longer)
- Bug 19910: Rip out optimistic data socks handshake variant (#3875)
- Bug 22564: Hide Firefox Sync
- Bug 25090: Disable updater telemetry
- Bug 26127: Make sure Torbutton and Tor Launcher are not treated as legacy extensions
- Bug 13575: Disable randomised Firefox HTTP cache decay user tests
- Bug 22548: Firefox downgrades VP9 videos to VP8 for some users
- Bug 24995: Include git hash in tor --version
- Bug 27268+27257+27262+26603 : Preferences clean-up
- Bug 26073: Migrate general.useragent.locale to intl.locale.requested
- Bug 27129+20628: Make Tor Browser available in ca, ga, id, is, nb, da, he, sv, and zh-TW
- Windows
- Bug 20636+10026: Create 64bit Tor Browser for Windows
- Bug 26381: Work around endless loop during page load and about:tor not loading
- Bug 27411: Fix broken security slider and NoScript interaction on Windows
- Bug 22581: Fix shutdown crash
- Bug 25266: PT config should include full names of executable files
- Bug 26304: Update zlib to version 1.2.11
- Update tbb-windows-installer to 0.4
- Bug 26355: Update tbb-windows-installer to check for Windows7+
- Bug 26355: Require Windows7+ for updates to Tor Browser 8
- OS X
- Linux
- Bug 22794: Don't open AF_INET/AF_INET6 sockets when AF_LOCAL is configured
- Bug 25485: Unbreak Tor Browser on systems with newer libstdc++
- Bug 20866: Fix OpenGL software rendering on systems with newer libstdc++
- Bug 26951+18022: Fix execdesktop argument passing
- Bug 24136: After loading file:// URLs clicking on links is broken on Linux
- Bug 24243: Tor Browser only renders HTML for local pages via file://
- Bug 24263: Tor Browser does not run extension scripts if loaded via about:debugging
- Bug 20283: Tor Browser should run without a `/proc` filesystem.
- Bug 26354: Set SSE2 support as minimal requirement for Tor Browser 8
- Build System
- All
- Bug 26362+26410: Use old MAR format for first ESR60-based stable
- Bug 27020: RBM build fails with runc version 1.0.1
- Bug 26949: Use GitHub repository for STIX
- Bug 26773: Add --verbose to the ./mach build flag for firefox
- Bug 26319: Don't package up Tor Browser in the `mach package` step
- Bug 27178: add support for xz compression in mar files
- Clean up
- Windows
- Bug 26203: Adapt tor-browser-build/tor-browser for Windows
- Bug 26204: Bundle d3dcompiler_47.dll for Tor Browser 8
- Bug 26205: Don't build the uninstaller for Windows during Firefox compilation
- Bug 26206: Ship pthread related dll where needed
- Bug 26396: Build libwinpthread reproducible
- Bug 25837: Integrate fxc2 into our build setup for Windows builds
- Bug 27152: Use mozilla/fxc2.git for the fxc2 repository
- Bug 25894: Get a rust cross-compiler for Windows
- Bug 25554: Bump mingw-w64 version for ESR 60
- Bug 23561: Fix nsis builds for Windows 64
- Bug 13469: Windows installer is missing many languages from NSIS file
- Bug 23231: Remove our STL Wrappers workaround for Windows 64bit
- Bug 26370: Don't copy msvcr100.dll and libssp-0.dll twice
- Bug 26476: Work around Tor Browser crashes due to fix for bug 1467041
- Bug 18287: Use SHA-2 signature for Tor Browser setup executables
- Bug 25420: Update GCC to 6.4.0
- Bug 16472: Update Binutils to 2.26.1
- Bug 20302: Fix FTE compilation for Windows with GCC 6.4.0
- Bug 25111: Don't compile Yasm on our own anymore for Windows Tor Browser
- Bug 18691: Switch Windows builds from precise to jessie
- OS X
- Bug 24632: Update macOS toolchain for ESR 60
- Bug 9711: Build our own cctools for macOS cross-compilation
- Bug 25548: Update macOS SDK for Tor Browser builds to 10.11
- Bug 26003: Clean up our mozconfig-osx-x86_64 file
- Bug 26195: Use new cctools in our macosx-toolchain project
- Bug 25975: Get a rust cross-compiler for macOS
- Bug 26475: Disable Stylo to make macOS build reproducible
- Bug 26489: Fix .app directory name in tools/dmg2mar
- Linux
- All